Category: Technology
Blue Tech Breakthroughs – Transforming Hydration with Advanced Purification
In the realm of technological innovation, Blue Tech is spearheading a revolution in the way we approach hydration, redefining the standards of water purification with cutting-edge advancements. Traditional water purification methods have often been associated with inefficiencies and limitations, but recent breakthroughs in Blue Tech are reshaping this landscape. Advanced purification technologies are at the forefront, seamlessly integrating into our daily lives to provide a safer and more sustainable water supply. One of the groundbreaking advancements in Blue Tech is the development of nanotechnology-based filtration systems. These systems operate at the molecular level, allowing for the removal of even the tiniest impurities and contaminants from water. Nano filters utilize specially engineered materials with Nano pores that effectively trap pollutants, bacteria, and viruses, ensuring that the water we consume is of the highest quality. This level of precision goes beyond traditional filtration methods, offering a level of purity previously thought unattainable.

Furthermore, Blue Tech is embracing the power of artificial intelligence AI to enhance water purification processes. Smart purification systems equipped with AI algorithms can analyze real-time data on water quality, adjusting filtration parameters accordingly. This dynamic adaptability ensures that the purification process is tailored to the specific contaminants present in the water, optimizing efficiency and minimizing resource usage. Additionally, AI-driven monitoring allows for proactive maintenance, ensuring the longevity and effectiveness of the purification systems. Another transformative aspect of Blue Tech in hydration is the utilization of sustainable materials in water purification technologies. Traditional methods often involve the use of disposable filters and chemical treatments that contribute to environmental degradation. Blue Tech seeks to address this issue by incorporating eco-friendly materials and reusable components in purification systems contact our team today. This not only reduces the environmental impact but also promotes a circular economy approach, aligning with global efforts to minimize waste and promote sustainability.
The integration of Internet of Things IoT technology is also reshaping the way we interact with water purification systems. Smart water purification devices can be connected to a network, allowing users to monitor water quality in real-time through mobile applications. Users can receive instant alerts about potential contaminants or when the filters need replacement, fostering a proactive approach to water quality management. This connectivity also facilitates remote control, enabling users to adjust purification settings and monitor system performance from anywhere, providing convenience and peace of mind. In conclusion, Blue Tech is not just transforming the way we hydrate; it is revolutionizing our approach to water purification. With nanotechnology, artificial intelligence, sustainable materials, and IoT integration, Blue Tech is creating a new era of water purification that is efficient, sustainable, and adaptable to the evolving needs of our society. As these breakthroughs continue to advance, the promise of a cleaner, safer, and more accessible water supply becomes increasingly attainable, paving the way for a healthier and more sustainable future.
Unlocking Potential – Access Control System as a Catalyst for Organizational Efficiency
In the fast-paced landscape of modern business, organizational efficiency is not merely a goal but a necessity. To stay competitive and adaptive, businesses are increasingly turning to advanced technologies to streamline their operations. One such technological innovation that stands out as a catalyst for organizational efficiency is the access control system. By seamlessly managing and monitoring access to physical and digital resources, access control system not only enhances security but also unlocks the full potential of an organization. At its core, an access control system is designed to regulate and monitor entry points, ensuring that only authorized personnel gain access to specific areas or information. This not only safeguards sensitive data and physical assets but also minimizes the risk of unauthorized activities. The impact on organizational efficiency is profound, as the system mitigates security concerns, allowing employees to focus on their tasks without distraction or concern. In a digital age where information is a valuable asset, protecting data is paramount. This not only reduces administrative overhead but also ensures accurate and reliable data for payroll processing.
Access control systems play a pivotal role in safeguarding digital assets by restricting access based on user roles and permissions. This ensures that only individuals with the necessary credentials can access sensitive information, reducing the likelihood of data breaches and unauthorized leaks. Consequently, organizations can operate with confidence, knowing that their intellectual property and confidential data are secure. Beyond digital security, access control system also enhances physical security by managing access to facilities and restricted areas. Traditional methods such as keys and manual access checks are not only prone to human error but also lack the agility needed in dynamic work environments. Access control systems, on the other hand, provide a flexible and efficient solution, allowing organizations to adapt quickly to changing access requirements. This agility not only prevents security lapses but also enables a seamless workflow, as employees can move freely within authorized areas without unnecessary delays. Furthermore, the integration of access control system with other organizational systems, such as time and attendance tracking or human resources databases, contributes to a more efficient and interconnected workplace.
For instance, access control systems san antonio can automate attendance recording, eliminating the need for manual timekeeping. In addition to security and efficiency gains, access control systems contribute to a positive organizational culture. By fostering a sense of trust among employees, access control system eliminates the need for constant supervision and micromanagement. This autonomy promotes a collaborative and empowered workforce, enhancing overall productivity and job satisfaction. The implementation of an access control system is a strategic investment that goes beyond mere security measures. It serves as a catalyst for organizational efficiency by streamlining access to both physical and digital resources. By mitigating security risks, enhancing workflow, and promoting a positive workplace culture, access control system unlocks the full potential of an organization in the competitive landscape of the modern business world. As businesses continue to evolve, the role of access control systems will undoubtedly become even more critical in shaping the efficiency and success of organizations across various industries.
Revolutionary Communication – Hosted PBX VoIP Strategies
Revolutionizing communication in the business landscape, Hosted Private Branch Exchange PBX Voice over Internet Protocol VoIP strategies have emerged as a game-changer, seamlessly integrating voice and data services over the internet. Unlike traditional phone systems, Hosted PBX VoIP operates in the cloud, offering businesses unparalleled flexibility, scalability, and cost-effectiveness. One key advantage lies in the elimination of the need for physical infrastructure. Hosted PBX VoIP systems operate through software and are hosted on external servers, reducing the burden on businesses to invest in and maintain extensive on-site equipment. This shift not only streamlines operations but also allows for easy scalability as businesses can add or remove users without the hassle of rewiring or configuring intricate hardware setups. Moreover, the flexibility afforded by Hosted PBX VoIP empowers businesses to embrace remote work seamlessly. With employees dispersed across various locations, the cloud-based system ensures that communication remains consistent and reliable.

The ability to connect to the PBX system from anywhere with an internet connection enables a dynamic and mobile workforce, enhancing productivity and collaboration. The cost-effectiveness of Hosted PBX VoIP is a pivotal factor in its widespread adoption. Traditional phone systems often entail hefty upfront costs for equipment and installation, not to mention ongoing maintenance expenses. In contrast, Hosted PBX VoIP operates on a subscription-based model, with businesses paying for the services they need. This pay-as-you-go approach eliminates the need for significant upfront investment, making it an attractive option for startups and small to medium-sized enterprises seeking to optimize their budget allocation. Security is another critical aspect addressed by Hosted PBX VoIP strategies. These systems typically come equipped with robust security features, including encryption and authentication protocols, safeguarding sensitive business communications. Providers also ensure regular updates and maintenance to protect against emerging cyber threats, offering businesses peace of mind in an increasingly digital and interconnected landscape.
Collaboration is enhanced through the integration of additional features within Hosted PBX voip for small business systems. Video conferencing, instant messaging, and other collaboration tools can be seamlessly integrated, fostering efficient communication within teams. This integrated approach not only simplifies operations but also creates a cohesive and connected work environment. In conclusion, Hosted PBX VoIP strategies represent a revolutionary shift in communication for businesses. With their cloud-based infrastructure, flexibility, cost-effectiveness, security features, and collaborative capabilities, these systems are reshaping the way businesses communicate, adapting seamlessly to the demands of a modern, dynamic work environment. As businesses continue to prioritize efficiency, scalability, and innovation, Hosted PBX VoIP strategies are poised to play a pivotal role in shaping the future of communication.
Streamline Manufacturing Efficiency with Particle Size Profiling
Particle size profiling plays a pivotal role in streamlining manufacturing efficiency across various industries. Understanding the distribution of particle sizes within raw materials or final products is crucial for optimizing processes, ensuring product quality, and reducing costs. By employing advanced particle size analysis techniques, manufacturers can achieve greater control over their operations and gain a competitive edge in the market. One of the primary benefits of particle size profiling is enhanced process control. In industries such as pharmaceuticals, food processing, and cosmetics, consistent particle size is critical to product quality. By monitoring particle size distribution throughout the manufacturing process, deviations can be quickly identified and corrected, ensuring that the final product meets specifications and regulatory requirements. This proactive approach minimizes the need for costly rework or product recalls, saving both time and resources. Moreover, particle size profiling enables manufacturers to optimize their production processes.
By understanding how particle size affects product characteristics, companies can make informed decisions about factors like mixing times, milling parameters, and material handling. This data-driven approach helps reduce production time, energy consumption, and raw material wastage, ultimately leading to cost savings and increased productivity. It also provides opportunities for continuous improvement, as manufacturers can fine-tune their processes based on real-time particle size data. Efficiency gains also extend to quality assurance. In industries where particle size directly impacts product performance, like in paints and coatings or the semiconductor industry, precise control over particle size is essential. By profiling particle size, manufacturers can maintain a consistently high level of product quality, reducing the likelihood of defects and customer complaints. This, in turn, strengthens their reputation and brand integrity. Additionally, particle size profiling supports research and development efforts. By understanding the particle size distribution of raw materials, researchers can make informed decisions about which materials to use in new product formulations.
This enables the creation of innovative, high-performance products that meet market demands, giving companies a competitive edge go and visit the site. Particle size analysis has also gained significance in environmental and safety aspects. In industries like mining and construction, understanding the particle size of dust and aerosols is crucial for protecting worker health and minimizing environmental impact. Effective particle size profiling helps in the development of dust control strategies, ensuring compliance with safety regulations and reducing environmental pollution. In conclusion, particle size profiling is an indispensable tool for streamlining manufacturing efficiency. It empowers manufacturers to maintain strict process control, optimize production, and ensure product quality. By providing real-time data on particle size distribution, companies can make informed decisions that lead to cost savings, improved product performance, and a stronger competitive position in the market.
CEO’s Guide to Robust Vendor Selection in Nearshore Outsourcing
In the present-day business climate Businesses are continuously seeking innovative strategies to stay competitive and efficient. One strategy that has seen considerable traction over the past few years is outsourcing nearshore. It involves working with software development and IT service providers in neighboring countries and bringing benefits such as cost savings, proximity, and an alignment of culture. In this piece, we look into the helpful information provided by CEOs on nearshore outsourcing, exploring their views and strategies to achieve the success of their ventures.
The CEO’s Perspective
The perspective of a CEO in the area of nearshore outsourcing is essential since it establishes the direction for the entire organisation. Chief executives are responsible for taking crucial decisions about the growth of the business, its cost structure and overall effectiveness. These are the most important insights given by CEOs
- Cost Optimization
CEOs have realized the savings potential in outsourcing to nearshore locations. Through leveraging the talent of neighboring countries with lower labor costs businesses can cut operating expenses and still maintain high quality standards. It allows them to devote the resources for other crucial parts of their business.
- Proximity and Time Zone Alignment
One of the major benefits of nearshore outsourcing is the geographic proximity. CEOs love the ease to work with teams located in the same time zone, which encourages collaboration and real-time communication. The proximity reduces the time it takes to wait and boosts productivity.
- Cultural Compatibility
Cultural alignment is another feature which CEOs consider important. Companies often find it easier to work with teams in near countries because of shared similarities in culture. This alignment can lead to more understanding, smoother process management and more effective results.
- Access to a Diverse Talent Pool
CEOs emphasize the importance of tapping into a diverse workforce. Nearshore outsourcing allows organizations to access a broad range of skills and expertise which is often difficult to access locally nearshore software development. This diversity can be an impetus for innovation and solving problems.

Strategies for Success
To maximise the value of nearshore outsourcing, CEOs adopt diverse strategies. They are designed to simplify operations and boost expansion:
- Robust Vendor Selection
The CEOs take their time when choosing the right outsourcing supplier. They search for companies with a proven track record with technical know-how, as well as dedication to excellence. A thorough due diligence process ensures a successful partnership.
- Clear Communication Channels
Establishing clear communication channels is vital. CEOs are committed to establishing transparent and transparent lines of communication between their in-house teams and the outsourced workforce. Regular meetings, progress updates and feedback systems are important.
- Risk Management
Risk management that is effective is a core component of the strategies of CEOs. They identify potential issues, such as language barriers or regulatory differences and are proactive in addressing those challenges. Plans for contingency and mitigation are in place to tackle unanticipated issues.
- Continuous Improvement
CEOs are adamant about fostering a culture that is constant enhancement. They ask for input from their team members and their outsourcing partners. They use this to develop procedures and improve collaboration. Continuous enhancements ensures that they will be successful for the long haul.
The CEOs also are the key players in shaping the strategy and direction of initiatives to outsource nearshore. Their perspectives highlight the many advantages of outsourcing to nearshore, including cost optimization close proximity, connectivity to culture, as well as access to talent from all over the world. With the help of robust strategies, CEOs open ways for effective partnerships which drive growth and innovation, making nearshore outsourcing a essential element of modern-day business practices. CEO Insights on Nearshore Outsourcing: Perspectives and Strategies.
The D3d12.dll Error Fix – The Best Technique That Solves DLL Errors
DLL errors are usually likely the most famous issues for Windows computer and are very bothersome. They are a problem on Windows even so lengthy the structure continues to be provided, as well as fix the situation, you will discover an easy stunt that you can do. The best procedure for fix DLL errors is usually to fix the pieces of Windows that are inducing the concern. DLL files indicate Dynamic Link Libraries and therefore are essentially little files which contain a growth of directions that an array of projects can utilize. These files were familiar in Windows ’98 with always keep programs from taking up an extreme amount of hard disk drive space by placing each of the standard capacities into these.dll files. Every program you utilize on Windows utilizes DLL guide files to assist them to work. Probably the very best example of the files in real life may be the capabilities it will require to support a program with interfacing the Internet.
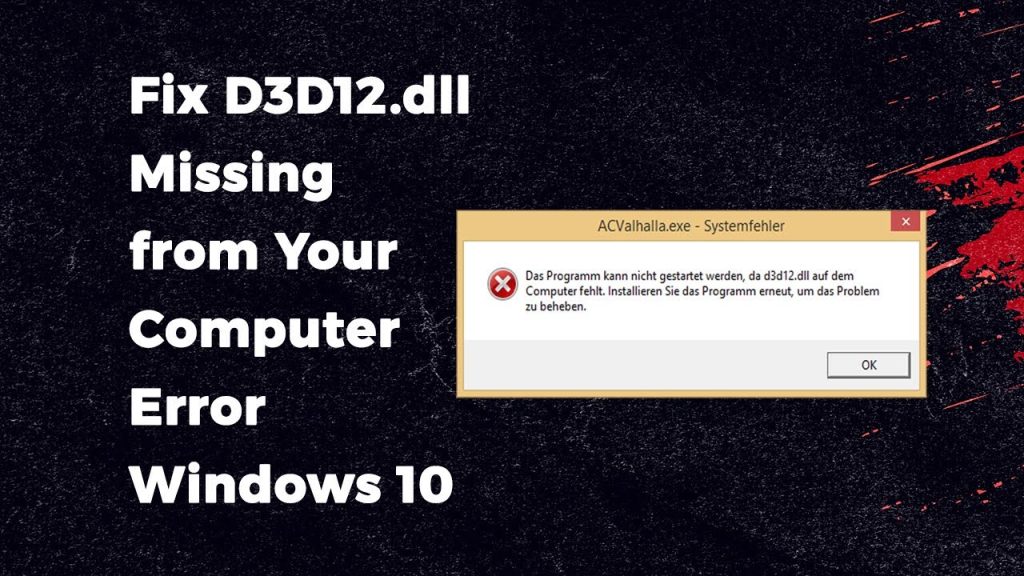
All the go to programs you may have, as Skype, Objective and MSN all depend on particular .dll files to assist these with interfacing with all the web, as well as the outline why.dll errors are induced this is certainly around the reasons that a substantial large amount of the files these projects require may become harmed, defiled or dropped. The problem you will be viewing is that at whatever point you must employ a program, it really is specifications to utilize d3d12.dll files together with the target for doing it to perform. Precisely what is more, amazingly, Windows carries a propensity for supplanting these files with a lot more set up adaptations or perhaps dropping the files, leading them to be unfit to get loaded. This makes your PC come to be incapable to peruse the files it requires, dialing it rear and leading to it to have distinct .DLL errors. To fix d3d12.dll errors, you should fix the bad file along with the personal references that Windows must that file.
Dll is actually an important file on the Windows Functioning System. It alludes to the Dynamic Link Library containing code or data used by a variety of projects or applications. The Dll files are relocated in your framework together with the organization of projects or applications. Dll errors take place when this type of addiction is bust or overwritten by diverse projects. Additionally, this can be totally completed a registry cleaner’ and that is an item musical instrument that sweeps with the platform files of Windows and fixes the entirety from the harmed files that are inside it. These units functionality to fix DLL errors while they supplant each of the obsolete DLL files are with brand new ones and correct the methods that Windows has to the files. You are able to download these units off the Internet and allow those to clean via your PC. They will highlight the quantity of errors which are inside it and allow you to fix them.
Financial Crimes – Expert Assistance for Fraud Detection
In today’s complex and interconnected financial landscape, combatting financial crimes has become an increasingly critical priority for organizations and governments worldwide. Fraud detection, in particular, stands out as a crucial aspect of this ongoing battle. To effectively identify and prevent fraudulent activities, businesses and institutions require expert assistance that combines advanced technologies, comprehensive strategies, and a deep understanding of evolving criminal tactics. One of the key challenges in combatting financial crimes is the ever-evolving nature of fraud. Fraudsters constantly adapt their techniques, leveraging technology advancements and exploiting vulnerabilities in systems and processes. As a result, traditional methods of fraud detection are often insufficient, necessitating the expertise of specialists who can stay one step ahead of criminals. These experts possess an intricate understanding of fraud patterns and employ cutting-edge tools, such as artificial intelligence (AI), machine learning, and data analytics, to detect suspicious activities and anomalies in large volumes of financial data.

By harnessing the power machine learning algorithms, expert fraud detection systems can continuously learn from vast datasets, identify complex patterns, and uncover previously undetectable schemes click fraud detection algorithm. These technologies analyze a multitude of data points, including transaction histories, customer behaviors, and contextual information, to build comprehensive profiles and flag suspicious activities. Furthermore, they can adapt in real-time, recognizing new fraud patterns and adjusting their algorithms accordingly to provide enhanced detection capabilities. In addition to advanced technologies, expert assistance in combatting financial crimes involves the formulation of comprehensive strategies tailored to the specific needs of organizations. These strategies encompass a holistic approach, considering prevention, detection, investigation, and response. Experts collaborate closely with businesses to assess vulnerabilities, design robust internal controls, and establish risk management frameworks. They provide guidance on implementing strong authentication protocols, fraud monitoring systems, and employee training programs, creating a multi-layered defense against fraudulent activities.
The fight against financial crimes also necessitates collaboration between public and private sectors. Experts play a vital role in facilitating information sharing and cooperation among financial institutions, regulatory bodies, law enforcement agencies, and other stakeholders. By fostering partnerships and establishing secure channels for communication, experts contribute to the rapid dissemination of intelligence, enabling proactive measures to prevent fraud schemes from proliferating across different sectors and jurisdictions. In conclusion, combatting financial crimes, particularly fraud detection, requires expert assistance that combines advanced technologies, comprehensive strategies, and collaboration among various stakeholders. These experts leverage AI, machine learning, and data analytics to identify evolving fraud patterns and deploy tailored solutions to protect organizations from financial losses. By staying ahead of the ever-adapting tactics of fraudsters, expert assistance plays a crucial role in safeguarding the integrity of financial systems and maintaining trust in the digital economy.
Photodiode Semiconductor – But to discover more about it
Tunable Diode Laser Spectroscopy is definitely an exploration place method that permits vaporous substances being considered if you use a laser. Alongside section of its existence, the attributes of the components are additionally accepted, which can be fully used to give far more unambiguous details towards the examiner also. Such attributes consolidate most excessive deluge, strain, and temperatures, along with the rate of petrol. Tunable Diode Laser beam functions by providing the laser beam entry the spectroscopy support the mechanism with this current situation the atmosphere getting tried out – – how the laser beam bar’s way goes by. The sunshine provider from your laser light is transformed as outlined by grant reviews and contains the option to conclude the gas provide in addition to their obsessions. The Tunable Diode Laser beam is viewed as an extremely accommodating and crucial thing in Real technology and Technology analysis as it might give each of the massive and crucial details that you can shape and present an outcome that is certainly correct.
Tunable Diode Laser can be a considerable section of the time employed in telecom products, assessing equipment and normalized label examines photodiode. They are in the same manner every single now and again considered as laser beam pointers in identifiable assortments that are a large section of the time possibly environmentally friendly or red-colored. Numerous functions for that Tunable Diode Laser are on Conservative dish player that distinguishes the Creeps and violet pillars which are a sizable section of the time found in scrutinizing Blue Club Sectors. There may be in addition robust laser beam Photodiode, photodiode types which are constantly used for added hypersensitive capacities. One particular qualified product is in the field of treatments by which laser beam Photodiode are every single now and once again employed for managing illnesses; and concentrating on legitimate attribute, for instance, hair departures and non-careful liposuction whereby the laser light is typically used to consume the saturated fats without the need for genuinely opening your body.
At this point, laser light Photodiode have made alone colossal in daily presence in different techniques achievable. It may have at first began as being an post that may be substantial basically on investigation areas, but as Science and Growth propels, the entire world finds a regularly increasing quantity of issues, a massive component of which will need extensive acknowledgment. Laserlight diode, with being able to conveniently maintain method, is actually a specifically helpful and supportive following substance certainly, and get guarantee that long term, its ease and comfort to individuals continues to increase far more and work on far more to make sure that men and women will really need to reside gladly and positively the most effective way possible.
Top Factors You May Need a Data Recovery Application or Service
Every morning you head into your working environment and fire up the notebook or other workplace computer. You go get coffee and have your early morning walk throughout the office. When investing in straight back to examine your e-mail, the truth is an unrecoverable mistake on the screen indicating your computer has a serious disk problem. You reboot a few times to find out if it just a temporary concern and each time you start to panic a growing number of as you may bear in mind you have vast amounts of data on our device which was by no means backed up to your network. Some of this data might even be related to personal family member’s images of your respective previous vacation. Ouch!
Anxiety begins to place in while you call your IT department and the one thing they may do is order another one drive to help you rear working. Your data is toast, or is it? Data recovery and Forensic Analysis is surely a place that made a great progress way over time as hard drives are getting to be more compact, faster and less costly and able to carry vast amounts of data. Of course the ideal contingency against data loss has incremental or full back ups done on a regular basis, but when you are one of those mavericks who only enter in the business office now and once more the majority of the back-up responsibility will likely be upon you. As you store more and more info on your equipment, you run the chance of losing it if your hard drive tanks.
You have a hard drive collision. Even though your hard drive is a lot more reputable than their predecessors, these are nevertheless technical and will crash periodically. The actuator left arm may become flawed or possibly a strength increase might take out of the drive control so you have a disk that could not work. You by accident delete data files on your hard drive and only understand the things you have performed long after the deed continues to be completed. Most people can easily enter in the recycle basket to access outdated files should they deleted them through the desktop computer or other area, but had you been industrious 1 day and began deleting volume amounts of data then purged your recycle container your files is probably not recoverable by way of classic indicates. A computer virus is taking control over your unit and possesses formatted your hard disk, simply to give you a big unfilled drive.
To sum up, possessing routine backups of the equipment is the greatest strategy in avoiding data loss. However, if you want to recover data there is certainly software and firms that offer data recovery professional services. Whatever direction you are going, the chances are pretty high that you may be able to recover your lost data files based on the situation.
Organizations Taking Tweaked Software Development Template
Taking into account the particular necessities of a business, software development organizations are offering reasonable custom software arrangements that can meet their particular prerequisites inside financial plan. The custom arrangements are assisting organizations with further developing their interior cycles that can use their true capacity in the specialty market. Assuming you have a comparable prerequisite, you can contact a reasonable software application development firm that gives quality modified software arrangements. While the software applications development firm intends to satisfy your particular business needs, they would search for a choice that is not just of good quality yet in addition practical by saving time and assets proficiently. The vast majority of the software firms follow a specific methodology that assists with distinguishing necessities and satisfies them with powerful software development administrations. We should know the primary concerns:
- Exhaustive Investigation of Client’s Requests and Business Prerequisites
- Plan out A Compelling Software Development Life Cycle SDLC
- Examine the Traps In order to Determine Them Brilliantly
- Foster Custom Software to Satisfy the Necessities
- SDLC Execution for Ideal Conveyance
The software application development firms have skill to plan an answer in the remarkable manner that can assist organizations with getting upper hand in the business DevOps process CI CD presentation by HiSlide.io. As the opposition is high, the greater part of the organizations is taking the assistance of experienced software template organizations. This makes it more critical to recruit a reasonable organization that does not just profess to offer great outcomes yet additionally gives practical outcomes to further develop business processes, group coordinated effort and business yield.
While you are marking an arrangement with the firm, you should make a note of things to ask from them. One of the primary elements is to get some information about the software customization. In the event that they are prepared to satisfy your business needs with redid software development administrations, you should realize about their involvement with involving different software innovations for fostering an answer.
When you are certain that you have seen as a reasonable template, you can examine your prerequisites with software designers to begin anticipating your SDLC. The powerful arranging will be a confirmation for your firm that you would get without bugs arrangements inside a specified time span. With custom software application development template arrangement, you will actually want to give better client care by keeping up with and coordinating your inner business information easily. it is essential to distinguish your necessities in advance so the software application designers can give a reasonable answer for meet your careful business needs as soon as could really be expected.
